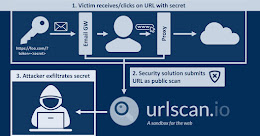
CISA Warns of Critical Vulnerabilities in 3 Industrial Control System Software
|
Older messages
CISA Warns of Critical Vulnerabilities in 3 Industrial Control System Software
Saturday, November 5, 2022
The Hacker News Daily Updates Newsletter cover Supply Chain Security Checklist Follow these steps to strengthen your organization's supply chain security and reduce your risk. Download Now
CISA Warns of Critical Vulnerabilities in 3 Industrial Control System Software
Friday, November 4, 2022
The Hacker News Daily Updates Newsletter cover Cybersecurity Budget Tips that Deliver the Most Bang for Your Buck Discover the data behind which cybersecurity controls deliver the best ROI Download Now
Hackers Using Rogue Versions of KeePass and SolarWinds Software to Distribute RomCom RAT
Thursday, November 3, 2022
The Hacker News Daily Updates Newsletter cover Get Proactive: How to Build a Resilient Cybersecurity Program Learn how to get proactive about your organization's cybersecurity posture to prevent
Cloud Security Handbook ($41.99 Value) FREE for a Limited Time
Wednesday, November 2, 2022
The Hacker News eBook Update Newsletter Cloud Security Handbook ($41.99 Value) FREE for a Limited Time Download For Free Securing resources in the cloud is challenging, given that each provider has
OpenSSL Releases Patch for 2 New High-Severity Vulnerabilities
Wednesday, November 2, 2022
The Hacker News Daily Updates Newsletter cover How to Build a Security Operations Center (On a Budget) Whether you're protecting a bank or the local grocery store, certain common sense security
You Might Also Like
CD#547 Writing a .NET profiler in C#
Sunday, March 9, 2025
CPU profiler for .NET using Silhouette ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏
RD#496 Signals in React?
Sunday, March 9, 2025
Not a good idea according to Filipe ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏
PD#616 Bloom Filter: A Deep Dive
Sunday, March 9, 2025
How Bloom filters are useful in scenarios with memory constraints ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏
Daily Coding Problem: Problem #1713 [Hard]
Sunday, March 9, 2025
Daily Coding Problem Good morning! Here's your coding interview problem for today. This problem was asked by Netflix. Implement a queue using a set of fixed-length arrays. The queue should support
Netflix codes/Travel Adapter/Real China
Sunday, March 9, 2025
Recomendo - issue #453 ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏
Sunday Digest | Featuring 'The 15 Largest Defense Budgets in the World' 📊
Sunday, March 9, 2025
Every visualization published this week, in one place. ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏
Android Weekly #665 🤖
Sunday, March 9, 2025
View in web browser 665 March 9th, 2025 Articles & Tutorials Sponsored Discover How AI Enables Zero-Maintenance Apps Watch Instabug's CPO, Kenny Johnston in this recorded webinar as he
😸 vibe coding is so in
Sunday, March 9, 2025
no more sunday scaries 🫶 Product Hunt Sunday, Mar 09 The Roundup This newsletter was brought to you by Rho no more sunday scaries 🫶 gm besties and welcome back to the Roundup. Today,. we're diving
This Week's Daily Tip Roundup
Sunday, March 9, 2025
Missed some of this week's tips? No problem. We've compiled all of them here in one convenient place for you to enjoy. Happy learning! iPhoneLife Logo View In Browser Your Tip of the Day is
The Sequence Radar #506: Honor to Whom Honor is Due: AI Won the Nobel Prize of Computing
Sunday, March 9, 2025
Some of the pioneers in reinforcement learning received the top award in computer science. ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏