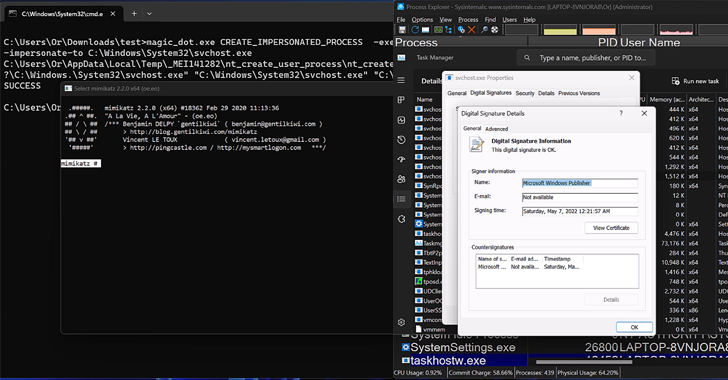
Researchers Uncover Windows Flaws Granting Hackers Rootkit-Like Powers
|
Older messages
Akira Ransomware Gang Extorts $42 Million; Now Targets Linux Servers
Saturday, April 20, 2024
THN Daily Updates Newsletter cover Webinar -- The Future of Threat Hunting Is Powered by Generative AI From Data to Defense: Step Into the Next Era of Cybersecurity with CensysGPT Download Now
Akira Ransomware Gang Extorts $42 Million; Now Targets Linux Servers
Friday, April 19, 2024
THN Daily Updates Newsletter cover Webinar -- The Future of Threat Hunting Is Powered by Generative AI From Data to Defense: Step Into the Next Era of Cybersecurity with CensysGPT Download Now
Beware: New Android Trojan 'SoumniBot' Evades Detection with Clever Tricks
Thursday, April 18, 2024
THN Daily Updates Newsletter cover Webinar -- Supply Chain Under Siege: Unveiling Hidden Threats Stop playing defense--start hunting threats. Protect your software supply chain with proactive
Comply with Google & Yahoo's New 2024 Email Authentication Requirements
Wednesday, April 17, 2024
Protect your domain from phishing and spoofing with PowerDMARC
Critical Atlassian Flaw Exploited to Deploy Linux Variant of Cerber Ransomware
Wednesday, April 17, 2024
THN Daily Updates Newsletter cover Windows Server 2022 & PowerShell All-in-One For Dummies ($30.00 Value) FREE for a Limited Time All the essentials for administering Windows Server 2022 in one
You Might Also Like
📱 Issue 453 - Does iOS have sideloading yet?
Thursday, March 6, 2025
This week's Awesome iOS Weekly Read this email on the Web The Awesome iOS Weekly Issue » 453 Release Date Mar 06, 2025 Your weekly report of the most popular iOS news, articles and projects Popular
💻 Issue 452 - Pro .NET Memory Management 2nd Edition
Thursday, March 6, 2025
This week's Awesome .NET Weekly Read this email on the Web The Awesome .NET Weekly Issue » 452 Release Date Mar 06, 2025 Your weekly report of the most popular .NET news, articles and projects
💎 Issue 459 - What's the Deal with (Ruby) Ractors?
Thursday, March 6, 2025
This week's Awesome Ruby Newsletter Read this email on the Web The Awesome Ruby Newsletter Issue » 459 Release Date Mar 06, 2025 Your weekly report of the most popular Ruby news, articles and
💻 Issue 459 - 7 Best Practices of File Upload With JavaScript
Thursday, March 6, 2025
This week's Awesome Node.js Weekly Read this email on the Web The Awesome Node.js Weekly Issue » 459 Release Date Mar 06, 2025 Your weekly report of the most popular Node.js news, articles and
💻 Issue 459 - TanStack Form V1 - Type-safe, Agnostic, Headless Form Library
Thursday, March 6, 2025
This week's Awesome JavaScript Weekly Read this email on the Web The Awesome JavaScript Weekly Issue » 459 Release Date Mar 06, 2025 Your weekly report of the most popular JavaScript news, articles
💻 Issue 454 - Take a break: Rust match has fallthrough
Thursday, March 6, 2025
This week's Awesome Rust Weekly Read this email on the Web The Awesome Rust Weekly Issue » 454 Release Date Mar 06, 2025 Your weekly report of the most popular Rust news, articles and projects
💻 Issue 377 - TanStack Form V1 - Type-safe, Agnostic, Headless Form Library
Thursday, March 6, 2025
This week's Awesome React Weekly Read this email on the Web The Awesome React Weekly Issue » 377 Release Date Mar 06, 2025 Your weekly report of the most popular React news, articles and projects
📱 Issue 456 - Safer Swift: How ~Copyable Prevents Hidden Bugs
Thursday, March 6, 2025
This week's Awesome Swift Weekly Read this email on the Web The Awesome Swift Weekly Issue » 456 Release Date Mar 06, 2025 Your weekly report of the most popular Swift news, articles and projects
JSK Daily for Mar 6, 2025
Thursday, March 6, 2025
JSK Daily for Mar 6, 2025 View this email in your browser A community curated daily e-mail of JavaScript news Build a Dynamic Watchlist for Your Web App with Angular & GraphQL (Part 6) In this
Charted | Disposable Income Growth of G7 Countries (2007-2024) 📈📉
Thursday, March 6, 2025
Among G7 countries, the US and Canada saw the largest increases in household disposable income since 2007. View Online | Subscribe | Download Our App Invest in your growth at Exchange 2025. FEATURED