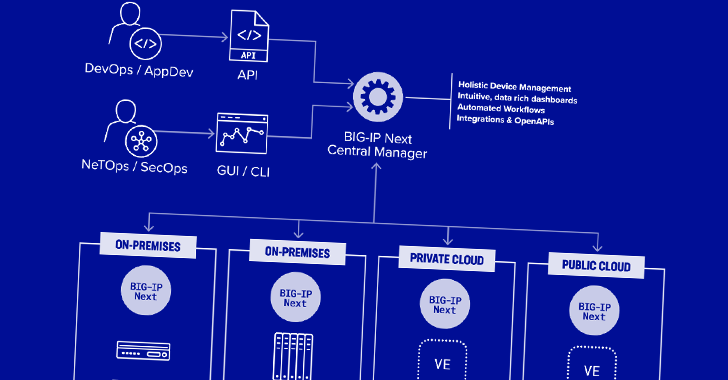
Warning: Critical F5 Central Manager Vulnerabilities Allow Enable Full Device Takeover
|
Older messages
How To Manage GenAI Security Risks
Wednesday, May 8, 2024
Managing GenAI Risks with SSPM Here to stay, GenAI tools are introducing new SaaS security risks. Employees often misplace their trust in easily accessible GenAI tools to automate work, without
Hijack Loader Malware Employs Process Hollowing, UAC Bypass in Latest Version
Wednesday, May 8, 2024
THN Daily Updates Newsletter cover Webinar -- The Future of Threat Hunting Is Powered by Generative AI From Data to Defense: Step Into the Next Era of Cybersecurity with CensysGPT Download Now
Critical UNPATCHED Tinyproxy Flaw Opens Over 50,000 Hosts to Remote Code Execution
Tuesday, May 7, 2024
THN Daily Updates Newsletter cover Webinar -- The Future of Threat Hunting Is Powered by Generative AI From Data to Defense: Step Into the Next Era of Cybersecurity with CensysGPT Download Now
Microsoft Outlook Flaw Exploited by Russia's APT28 to Hack Czech, German Entities
Monday, May 6, 2024
THN Daily Updates Newsletter cover Webinar -- Data Security is Different at the Petabyte Scale Discover the secrets to securing fast-moving, massive data sets with insights from industry titans
Microsoft Outlook Flaw Exploited by Russia's APT28 to Hack Czech, German Entities
Saturday, May 4, 2024
THN Daily Updates Newsletter cover Webinar -- Data Security is Different at the Petabyte Scale Discover the secrets to securing fast-moving, massive data sets with insights from industry titans
You Might Also Like
The Sequence Opinion #504: Does AI Need New Programming Languages?
Thursday, March 6, 2025
And some old computer science theories that can become sexy again in the era of AI-first programming languages. ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏
U.S. Charges 12 Chinese Nationals in State-Backed Hacking Operations
Thursday, March 6, 2025
THN Daily Updates Newsletter cover ⚡ LIVE WEBINAR ➟ ASPM: The Future of AppSec -- Boom or Bust? Discover How ASPM is Redefining Application Security with Smarter, Unified Solutions. Download Now
Is it time for you to get a VPN?
Thursday, March 6, 2025
Hello there, Most people don't think twice about online tracking. But the truth is, it's not just about targeted ads. Cybercriminals and scammers have ways of using your internet traffic
🚴🏼♂️ Apple Should Make an Electric Bike — 10 Cars That Were Technologically Ahead Of Their Time
Thursday, March 6, 2025
Also: iPhone 16e Review, and More! How-To Geek Logo March 6, 2025 Did You Know The cat in the opening scene of The Godfather purred so loudly that some of the lines in the scene had to be redubbed. 💻
📧 Did you want this discount?
Thursday, March 6, 2025
Hey, it's Milan. I want to make sure you see this today because it may be gone this weekend: There are 29 coupons left to join Pragmatic REST APIs with 30% off. After that, the price goes back to
Tiny Type On Yellow Pages ☎️
Thursday, March 6, 2025
That time phone books got a font upgrade. Here's a version for your browser. Hunting for the end of the long tail • March 5, 2025 Tiny Type On Yellow Pages Why AT&T had to redesign its primary
Simplify Kotlin Error Handling
Thursday, March 6, 2025
View in browser 🔖 Articles Goodbye try-catch, Hello runCatching! Exception handling in Kotlin just got cleaner! This article explores how runCatching can replace traditional try-catch blocks, making
JSK Daily for Mar 5, 2025
Wednesday, March 5, 2025
JSK Daily for Mar 5, 2025 View this email in your browser A community curated daily e-mail of JavaScript news Unions and intersections of object types in TypeScript In this blog post, we explore what
Daily Coding Problem: Problem #1709 [Medium]
Wednesday, March 5, 2025
Daily Coding Problem Good morning! Here's your coding interview problem for today. This problem was asked by Facebook. Given an array of integers, write a function to determine whether the array
How Swiss Tables make Go 1.24 faster
Wednesday, March 5, 2025
Plus a way to call external library functions without Cgo. | #544 — March 5, 2025 Unsub | Web Version Together with pgAnalyze Go Weekly Faster Go Maps with Swiss Tables — One of Go's newest