Issue 84: Unprotected APIs at Google Firebase, leaky Arkansas PUA portal💦
|
|||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
Older messages
Issue 83: India’s COVID-19 tracing app 🦠, OAuth2 API attacks
Thursday, May 14, 2020
Hi, this week we look at API vulnerabilities in coronavirus tracking, OAuth2 security APIsecurity.io The Latest API Security News, Vulnerabilities and Best Practices Issue: #83 India's COVID-19
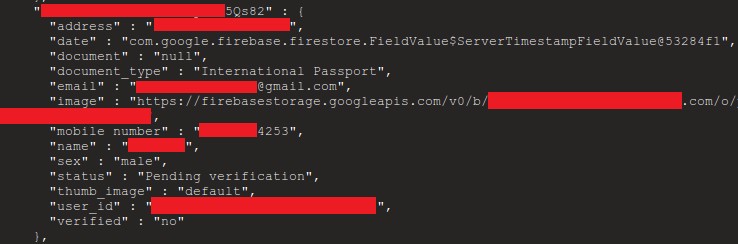
Issue 82: Most common GraphQL vulnerabilities, pentesting with Insomnia
Thursday, May 7, 2020
Hi, this week we look at GraphQL security, pentesting with Insomnia, OAuth2 cheetsheets APIsecurity.io The Latest API Security News, Vulnerabilities and Best Practices Issue: #82 Most common GraphQL
Issue 81: Vulnerabilities in Microsoft Teams 👥, Auth0, smart home hubs
Thursday, April 30, 2020
Hi, this week, we check out how Microsoft Teams could be breached with a single GIF APIsecurity.io The Latest API Security News, Vulnerabilities and Best Practices Issue: #81 Vulnerabilities in
Issue 80: API vulnerabilities IBM DRM and Cisco USC ☎️
Thursday, April 23, 2020
Hi, this week, we look at API vulnerabilities in IBM and Cisco products, and upcoming APIsecurity.io The Latest API Security News, Vulnerabilities and Best Practices Issue: #80 API vulnerabilities IBM
Issue 79: 1.4 million doctor records scraped using API 👩⚕️
Thursday, April 16, 2020
Hi, this week we look at recent vulns at GitLab and findadoctor.com, conference talk APIsecurity.io The Latest API Security News, Vulnerabilities and Best Practices Issue: #79 1.4 million doctor
You Might Also Like
Spyglass Dispatch: Meta Miscues
Wednesday, January 8, 2025
Meta's Social AI Content • Anthropic at $60B • Bluesky at $700M • Dick Wolf's 30 Minute Show • NVIDIA's CPU Aspirations The Spyglass Dispatch is a newsletter sent on weekdays featuring
Top Tech Deals 💰 Anker Power Station, GoPro, 8BitDo Controller, and More!
Wednesday, January 8, 2025
Upgrade your life with a new power station, Wi-Fi 7 router, or AirTags at a big discount. How-To Geek Logo January 8, 2025 Top Tech Deals: Anker Power Station, GoPro Hero, 8BitDo Controller, and More!
Is Claude.ai worth $60 billion? 🎩
Wednesday, January 8, 2025
+ AI will mow my lawn ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏
Post from Syncfusion Blogs on 01/08/2025
Wednesday, January 8, 2025
New blogs from Syncfusion Effortlessly Manage Large File Uploads with Blazor File Manager By Keerthana Rajendran This blog explains the new chunk upload feature added in the Blazor File Manger
⚙️ Waymo's big moment
Wednesday, January 8, 2025
The road to AGI
The best AI tech of CES 2025
Wednesday, January 8, 2025
✨ A Linux desktop for AI devs; OTC CGMs; Big Delta upgrades -- ZDNET ZDNET Tech Today - US January 8, 2025 Robotics and AI tech at CES 2025 shown on a universe colorful background. The best robotics
[Guide] AWS Security Essentials in Two Steps
Wednesday, January 8, 2025
Download the quick guide and take control of your AWS security now! The Hacker News The best AWS environments benefit from layered security and smart automation. Securing AWS environments is crucial
FCC Launches 'Cyber Trust Mark' for IoT Devices to Certify Security Compliance
Wednesday, January 8, 2025
THN Daily Updates Newsletter cover Generative AI, Cybersecurity, and Ethics ($88.00 Value) FREE for a Limited Time Equips readers with the skills and insights necessary to succeed in the rapidly
The Sequence Engineering #464: OpenAI’s Relatively Unknown Agent Framework
Wednesday, January 8, 2025
OpenAI Swarm provides the key building blocks for implementing agents. ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏
About-Face(book)
Wednesday, January 8, 2025
Mark Zuckerberg's new stance on speech can be both real and really political About-Face(book) Mark Zuckerberg's new stance on speech can be both real and really political By MG Siegler • 8 Jan