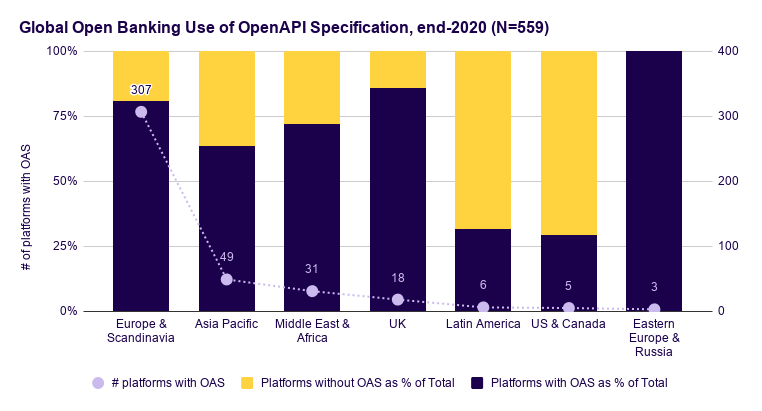
Issue 127: Hidden OAuth attack vectors, Methodology for BOLA/IDOR 🗝️
|
|||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
Older messages
Issue 126: F5 iControl REST API under attack, Regexploit, Ford’s API security talk recording 🚗
Thursday, March 25, 2021
Hi, today we look at a couple of recent API vulnerabilities, a new regex analysis tool APIsecurity.io The Latest API Security News, Vulnerabilities and Best Practices Issue: #126 F5 iControl REST API
Issue 125: iPhone call recorder API flaw, Burp and OpenAPI, GraphQL pentesting, FAPI 💱
Thursday, March 18, 2021
Hi, today we look at the just released FAPI 1.0, GraphQL pentesting, OpenAPI in Burp, APIsecurity.io The Latest API Security News, Vulnerabilities and Best Practices Issue: #125 iPhone call recorder
Issue 124: API vulnerabilities at Microsoft and Truecaller Guardians, Pentester labs, API security at Ford Motors 🚗
Saturday, March 13, 2021
Hi, this week we look at the recent brute-force attack on Microsoft's password reset, APIsecurity.io The Latest API Security News, Vulnerabilities and Best Practices Issue: #124 API vulnerabilities
Issue 123: API vulnerabilities VMWare vCenter and Facebook, mismatch between JSON parsers, API security fixes in VS Code
Thursday, March 4, 2021
Hi, this week we look at how URL caching and JSON parsing can bite you, and check out APIsecurity.io The Latest API Security News, Vulnerabilities and Best Practices Issue: #123 API vulnerabilities
Issue 122: API issues at Clubhouse 👋 and healthcare apps, scope-based recon, OAS v3.1.0
Thursday, February 25, 2021
Hi, this week we look at API vulnerabilities in Clubhouse and mHealth apps, recon & OAS APIsecurity.io The Latest API Security News, Vulnerabilities and Best Practices Issue: #122 API issues at
You Might Also Like
Data Science Weekly - Issue 579
Thursday, December 26, 2024
Curated news, articles and jobs related to Data Science, AI, & Machine Learning ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏
💎 Issue 449 - JRuby with JBang
Thursday, December 26, 2024
This week's Awesome Ruby Newsletter Read this email on the Web The Awesome Ruby Newsletter Issue » 449 Release Date Dec 26, 2024 Your weekly report of the most popular Ruby news, articles and
💻 Issue 449 - JavaScript Benchmarking Is a Mess
Thursday, December 26, 2024
This week's Awesome JavaScript Weekly Read this email on the Web The Awesome JavaScript Weekly Issue » 449 Release Date Dec 26, 2024 Your weekly report of the most popular JavaScript news, articles
📱 Issue 443 - EU asks for views on plan to force Apple to open up iOS
Thursday, December 26, 2024
This week's Awesome iOS Weekly Read this email on the Web The Awesome iOS Weekly Issue » 443 Release Date Dec 26, 2024 Your weekly report of the most popular iOS news, articles and projects Popular
💻 Issue 442 - SOLID: The Liskov Substitution Principle (LSP) in C#
Thursday, December 26, 2024
This week's Awesome .NET Weekly Read this email on the Web The Awesome .NET Weekly Issue » 442 Release Date Dec 26, 2024 Your weekly report of the most popular .NET news, articles and projects
Daily Coding Problem: Problem #1649 [Easy]
Thursday, December 26, 2024
Daily Coding Problem Good morning! Here's your coding interview problem for today. This problem was asked by Dropbox. Spreadsheets often use this alphabetical encoding for its columns: "A
JSK Daily for Dec 26, 2024
Thursday, December 26, 2024
JSK Daily for Dec 26, 2024 View this email in your browser A community curated daily e-mail of JavaScript news Performance Optimization in React Pivot Table with Data Compression The Syncfusion React
📱 Issue 446 - Fatbobman's Swift Weekly #063
Thursday, December 26, 2024
This week's Awesome Swift Weekly Read this email on the Web The Awesome Swift Weekly Issue » 446 Release Date Dec 26, 2024 Your weekly report of the most popular Swift news, articles and projects
💻 Issue 444 - Four limitations of Rust’s borrow checker
Thursday, December 26, 2024
This week's Awesome Rust Weekly Read this email on the Web The Awesome Rust Weekly Issue » 444 Release Date Dec 26, 2024 Your weekly report of the most popular Rust news, articles and projects
💻 Issue 367 - React 19: A New Era of Web Development
Thursday, December 26, 2024
This week's Awesome React Weekly Read this email on the Web The Awesome React Weekly Issue » 367 Release Date Dec 26, 2024 Your weekly report of the most popular React news, articles and projects