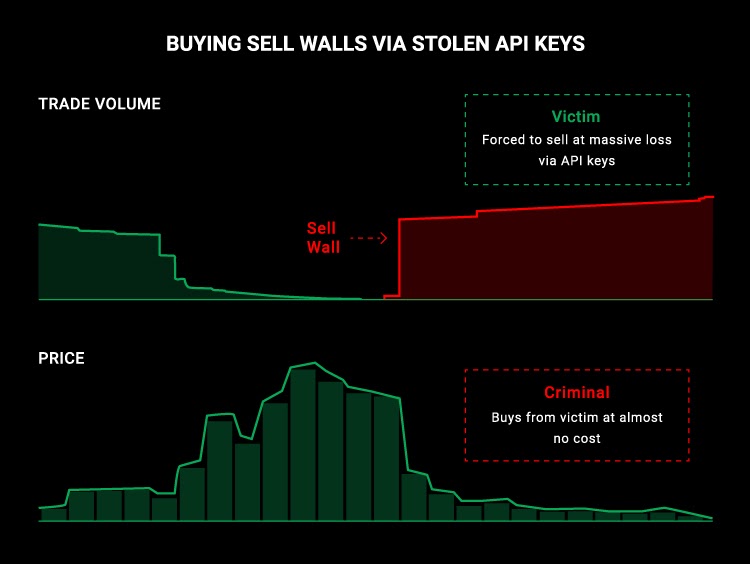
Issue 135: Millions stolen from cryptoexchanges through APIs 💱
|
|||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
Older messages
Issue 134: API vulnerabilities at Echelon, Instagram, Facebook Workspace
Thursday, May 20, 2021
Hi, today we look into details of 3 recent API vulnerability reports and have an RSCA interview with Forrester's Sandy Carielli APIsecurity.io The Latest API Security News, Vulnerabilities and Best
Issue 133: Vulnerable Peloton APIs, API contract generation for .NET 💻
Friday, May 14, 2021
Hi, this week we look at Peloton and India's CoWIN, OpenAPI contracts based on .NET annotations, API Security sessions at RSAC AppSec Village APIsecurity.io The Latest API Security News,
Issue 132: Experian API leak, breaches at DigitalOcean and Geico, Burp plugins, vAPI lab
Thursday, May 6, 2021
Hi, this week we look at new API tools & recent Experian, DigitalOcean, Geiko, Facebook APIsecurity.io The Latest API Security News, Vulnerabilities and Best Practices Issue: #132 Experian API leak
Issue 131: API vulnerabilities at John Deere, Springfox, JWT lab, AutoGraphQL 🔎
Thursday, April 29, 2021
Hi, this week, we look at the recent API vulnerability in farming machinery and a few APIsecurity.io The Latest API Security News, Vulnerabilities and Best Practices Issue: #131 API vulnerabilities at
Issue 130: GitHub’s new token format, MindAPI, Kiterunner
Thursday, April 22, 2021
Hi, this week we look at API token best practices, and tools for API recon & pentesting APIsecurity.io The Latest API Security News, Vulnerabilities and Best Practices Issue: #130 GitHub's new
You Might Also Like
Help Shape the Future of Laravel News - Quick Survey
Friday, December 27, 2024
Help shape Laravel News - Quick 2-minute survey Hi there, As a valued member of the Laravel News community, we'd love to hear your thoughts to help us make our newsletter even better in 2025. Would
Data Science Weekly - Issue 579
Thursday, December 26, 2024
Curated news, articles and jobs related to Data Science, AI, & Machine Learning ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏
💎 Issue 449 - JRuby with JBang
Thursday, December 26, 2024
This week's Awesome Ruby Newsletter Read this email on the Web The Awesome Ruby Newsletter Issue » 449 Release Date Dec 26, 2024 Your weekly report of the most popular Ruby news, articles and
💻 Issue 449 - JavaScript Benchmarking Is a Mess
Thursday, December 26, 2024
This week's Awesome JavaScript Weekly Read this email on the Web The Awesome JavaScript Weekly Issue » 449 Release Date Dec 26, 2024 Your weekly report of the most popular JavaScript news, articles
📱 Issue 443 - EU asks for views on plan to force Apple to open up iOS
Thursday, December 26, 2024
This week's Awesome iOS Weekly Read this email on the Web The Awesome iOS Weekly Issue » 443 Release Date Dec 26, 2024 Your weekly report of the most popular iOS news, articles and projects Popular
💻 Issue 442 - SOLID: The Liskov Substitution Principle (LSP) in C#
Thursday, December 26, 2024
This week's Awesome .NET Weekly Read this email on the Web The Awesome .NET Weekly Issue » 442 Release Date Dec 26, 2024 Your weekly report of the most popular .NET news, articles and projects
Daily Coding Problem: Problem #1649 [Easy]
Thursday, December 26, 2024
Daily Coding Problem Good morning! Here's your coding interview problem for today. This problem was asked by Dropbox. Spreadsheets often use this alphabetical encoding for its columns: "A
JSK Daily for Dec 26, 2024
Thursday, December 26, 2024
JSK Daily for Dec 26, 2024 View this email in your browser A community curated daily e-mail of JavaScript news Performance Optimization in React Pivot Table with Data Compression The Syncfusion React
📱 Issue 446 - Fatbobman's Swift Weekly #063
Thursday, December 26, 2024
This week's Awesome Swift Weekly Read this email on the Web The Awesome Swift Weekly Issue » 446 Release Date Dec 26, 2024 Your weekly report of the most popular Swift news, articles and projects
💻 Issue 444 - Four limitations of Rust’s borrow checker
Thursday, December 26, 2024
This week's Awesome Rust Weekly Read this email on the Web The Awesome Rust Weekly Issue » 444 Release Date Dec 26, 2024 Your weekly report of the most popular Rust news, articles and projects