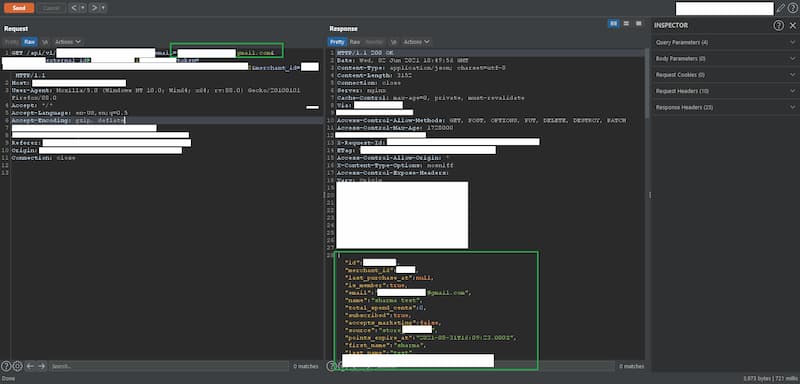
Issue 146: Facebook API leaking private group membership, JWT Attacker plugin for Burp
|
|||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
Older messages
Issue 145: APIs and electric car charging stations, The Nuts and Bolts of OAuth 2.0 🔩
Thursday, August 5, 2021
Hi, today we look at the recent EV charging station API vulnerabilities, an OAuth2.0 course in Udemy, Gartner API Hype Cycle, and API path tra APIsecurity.io The Latest API Security News,
Issue 144: JustDial API vulnerability re-emerges, API key checker, the state of OAuth
Thursday, July 29, 2021
Hi, this week we have great videos on OAuth roadmap and GraphQL attacks and defenses. There's also an API key validator script and a story of APIsecurity.io The Latest API Security News,
Issue 143: GraphQL API leaking credit cards, SQLi in JWT, XML attacks mind map 🗺️
Thursday, July 22, 2021
Hi, today we have a case study of an API leaking credit card numbers, a lab on SQL injections in JWT, an API Security CTF, and a mind map of APIsecurity.io The Latest API Security News, Vulnerabilities
Issue 142: API vulnerabilities in Coursera and Huawei, GraphQL rate limiting and discovery 🔎
Friday, July 16, 2021
Hi, this week we look at the recent vulnerabilities in Coursera & Huawei, and discuss rate-limiting best practices for GraphQL as well as new APIsecurity.io The Latest API Security News,
Issue 141: API vulnerabilities in VeryFitPro and Gettr, AWS Lambda authorizers, AsyncAPI 2.1 🏅
Saturday, July 10, 2021
Hi, today we have a few recent API vulnerability case studies, a research on possible implementation flaws in AWS Lambda Authorizers, and the APIsecurity.io The Latest API Security News,
You Might Also Like
Daily Coding Problem: Problem #1648 [Medium]
Wednesday, December 25, 2024
Daily Coding Problem Good morning! Here's your coding interview problem for today. This problem was asked by Quora. Given an absolute pathname that may have . or .. as part of it, return the
🎮 The Best Games to Go With Your New Console — Streaming Services Could Learn From YouTube
Wednesday, December 25, 2024
Also: Don't Throw Christmas Gift Boxes on the Curb, and More! How-To Geek Logo December 25, 2024 Did You Know Years before The Nightmare Before Christmas, Tim Burton was sprinkling references to
Charted | Global Economic Confidence in 2025, by Country 🌎
Wednesday, December 25, 2024
While emerging markets in Asia have the strongest confidence in the global economy looking ahead, European countries are most pessimistic. View Online | Subscribe | Download Our App FEATURED STORY
Top Tech Deals 🎅 Sony Headphones, iPhone Cases, 4K Projector, and More!
Wednesday, December 25, 2024
The season of giving is upon us. How-To Geek Logo December 25, 2024 Top Tech Deals: Sony Headphones, iPhone Cases, 4K Projector, and More! The season of giving is upon us. Happy Holidays! If you're
Why the Race to AGI is Humanitys Defining Moment
Wednesday, December 25, 2024
Top Tech Content sent at Noon! Boost Your Article on HackerNoon for $159.99! Read this email in your browser How are you, @newsletterest1? 🪐 What's happening in tech today, December 25, 2024? The
Iran's Charming Kitten Deploys BellaCPP: A New C++ Variant of BellaCiao Malware
Wednesday, December 25, 2024
THN Daily Updates Newsletter cover The Data Science Handbook, 2nd Edition ($60.00 Value) FREE for a Limited Time Practical, accessible guide to becoming a data scientist, updated to include the latest
Software Testing Weekly - Issue 251
Wednesday, December 25, 2024
GitHub Copilot is free! 🤖 View on the Web Archives ISSUE 251 December 25th 2024 COMMENT Welcome to the 251st issue! In case you missed it — GitHub Copilot is free! The free version works with Visual
Daily Coding Problem: Problem #1647 [Medium]
Tuesday, December 24, 2024
Daily Coding Problem Good morning! Here's your coding interview problem for today. This problem was asked by Square. In front of you is a row of N coins, with values v 1 , v 1 , ..., v n . You are
Sentiment Analysis, Topological Sort, Web Security, and More
Tuesday, December 24, 2024
Exploring Modern Sentiment Analysis Approaches in Python #661 – DECEMBER 24, 2024 VIEW IN BROWSER The PyCoder's Weekly Logo Exploring Modern Sentiment Analysis Approaches in Python What are the
🤫 Do Not Disturb Mode Is My Secret to Sanity — 8 Gadgets I Want To See Nintendo Make
Tuesday, December 24, 2024
Also: The Best Christmas Movies to Watch on Netflix, and More! How-To Geek Logo December 24, 2024 Did You Know Their association with the Christmas season might make you think poinsettias hail from a