Net Interest - Waiting for the Dog to Bark
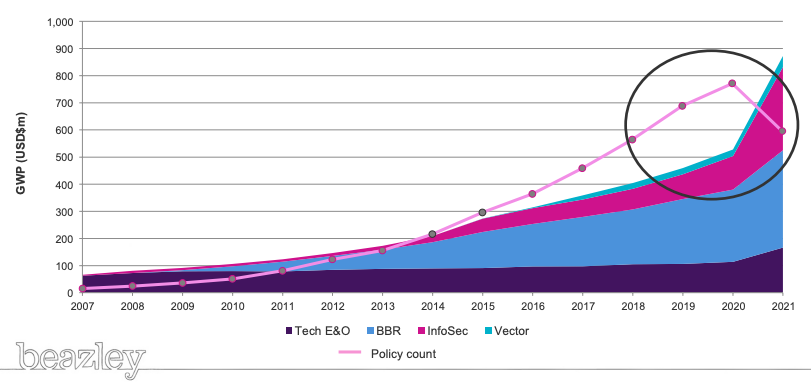
Five years before Russia launched its physical assault on Ukraine, it launched a digital assault. On June 27th, 2017, the day before a major public holiday, Ukrainians woke up to black screens everywhere. “They could not take money from ATMs, pay for gas at stations, send or receive mail, pay for a train ticket, buy groceries, get paid, or – perhaps most terrifying of all – monitor radiation levels at Chernobyl.” That’s according to Nicole Perlroth, whose book about cyber warfare won last year’s Business Book of the Year. The cause of the disruption was a piece of software called NotPetya. Exploiting vulnerabilities in Microsoft Windows, it worked its way through the country’s computer networks, grabbing passwords as it went. It was introduced into the country via an accounting and bookkeeping package used by 80% of Ukrainian firms. From there, a routine update set it on its way. System users would be greeted with a ransom demand, but that was only a ruse – NotPetya’s motive wasn’t greed, it was destruction. “By the second you saw it, your data center was already gone,” a security expert told Andy Greenberg, author of the book Sandworm. In its wake NotPetya took down at least four hospitals, six power companies, two airports, more than 22 Ukrainian banks, payment systems in retailers and transport, and practically every federal agency. According to cybersecurity company, Information Systems Security Partners, at least 300 companies were hit, and one senior Ukrainian government official estimated that 10% of all computers in the country were wiped. The damage wasn’t even restricted to Ukraine. Computers at pharma company Merck, shipping company Maersk, logistics company FedEx, and food company Mondelez, were all impacted. The Maersk outage led to downtime at port terminals around the world. Maersk had to rebuild its entire network of 4,000 servers and 45,000 PCs. Adding together the the cost of lost business, customer reimbursements and the network rebuild, the company’s chairman put losses at between $250 million and $300 million. In aggregate, NotPetya is estimated to have inflicted over $10 billion worth of damage in Ukraine and beyond. Since then, policymakers across the world have been on high alert, not least in the financial industry. “I would say that the risk that we keep our eyes on the most now is cyber-risk,” Federal Reserve governor Jerome Powell told an interviewer last year. “That’s really where the risk I would say is now, rather than something that looked like the global financial crisis.” Other central bankers agree. Their biannual financial stability reports regularly cite cyber as a key “known unknown” risk facing their financial systems. So when Russia launched its offensive last month, many people anticipated that it would be accompanied by a series of cyber attacks. In the run-up to the invasion, Ukraine was indeed hit. Some banks and government services were temporarily knocked offline, but it was nothing on the scale of NotPetya. My friend, fleeing from Kyiv, wrote to me: “I expected that bank and mobile systems could be destroyed.” A month later, he is still texting me via a functional cellular network. There are various reasons cyber attacks may not have been more punishing, one being that the Russian army is using local networks for its own communications. Yet there are increasing fears that as Russia intensifies its military efforts in Ukraine, it will ramp up digital efforts elsewhere in response to sanctions. This week, President Biden warned of “evolving intelligence that the Russian Government is exploring options for potential cyberattacks.” He said that while the US government will do what it can to deter such attacks, private companies should accelerate their efforts to “lock their digital doors.” What It Means for BanksBanks are especially vulnerable. Their role in the payments system makes them an attractive target and their interconnectedness magnifies overall risk. They also operate lots of devices – Citigroup revealed recently that it runs 740,000 devices. No surprise then that banks are high-value targets. According to Boston Consulting Group, financial services firms are 300 times as likely as other companies to be targeted by a cyber attack. US Banks have once before been victims of state-sponsored cyber attacks. While Russia is responsible for the majority of state-sponsored attacks – just under 60% in 2021 according to data from Microsoft – other states notably North Korea, Iran and China are also active. Back in 2011 and 2012, hackers from Iran targeted US banks including Bank of America, JPMorgan and Capital One. The hackers hijacked computers at data centres around the world and trained them on US banks in an attempt to overwhelm them with traffic so that they collapse under the load (so called “distributed denial-of-service” attacks). According to an indictment filed by the US Department of Justice, banks’ computer servers were hit with as much as 140 Gigabits of data per second, which was up to three times their operating capacity. As a result, hundreds of thousands of customers were unable to access their bank accounts online and banks incurred “tens of millions” of dollars in remediation costs. Such an attack can be classified as an attempt to compromise the availability of a bank’s data or systems. But this is just one of three categories of attack that hackers can unleash. In addition to compromising availability, hackers can compromise confidentiality or integrity. An attack on confidentiality is equivalent to a data breach, where hackers steal proprietary data; an attack on integrity seeks to amend data, sometimes for the hackers’ own financial benefit. Together these categories are known among cyber security professionals as the CIA Triad. The highest profile example of a confidentiality breach in the banking sector occurred at Capital One. In March 2019, a former Amazon Web Services software engineer brazenly accessed an AWS server that stored Capital One credit card data and stole information corresponding to 100 million card applications. She was caught touting the stolen data on GitHub and on social media. “I’ve basically strapped myself with a bomb vest,” she wrote in a Twitter DM, “fucking dropping capitol ones dox and admitting it.” Her trial resumed last week. For its part, Capital One was ordered to pay a fine of $80 million by regulators for neglecting to protect customer data. It also recently reached a $190 million settlement with customers. The best example of a financial data integrity breach took place in February 2016, when an attempt was made to steal $1 billion from the central bank of Bangladesh. Hackers used the SWIFT network to send fraudulent instructions requesting the transfer of funds out of the central bank’s account at the Federal Reserve Bank of New York. Most of the transactions were blocked – due to suspicions aroused by misspelt instructions – but five made it through, in an amount of $101 million. Some of the funds have been recovered, but over $60 million still remain at large. North Korea is assumed to be behind the attack. Banks invest very heavily to protect themselves from these risks. “Cyber has been a huge focus for a long time,” said the CFO of JPMorgan at a recent investor event. “We spend a lot of money on it… it’s not an area where you can afford to make mistakes… [but] it’s obviously not cheap.” Like any intelligence activity, it’s usually the failures of these defences that make it into the headlines rather than the successes, which makes it difficult to assess their efficacy. But a recent paper from the Bank for International Settlements concludes that while the financial sector is exposed to a larger number of cyber attacks, it suffers lower costs – a feature its authors put down to stronger defences. The problem – and this is what worries regulators – is what happens if cyber damage cascades through the financial system. The distribution of losses is already very skewed. Average cyber losses may be quite low but, as NotPetya demonstrated, tail losses can be very high. Overlay that distribution on an interconnected financial system, and problems could emerge, not dissimilar to those caused by other losses of confidence in the banking sector. In 2020, the New York Fed tried to model these effects. It conducted a “pre-mortem” analysis of cyber risk in the US financial system (like a post-mortem, except you do it beforehand). Researchers looked at the Fedwire wholesale payments network and analysed what would happen if banks were blocked from making payments. They found that a successful attack on one of the largest US banks could interrupt between 5% and 35% of daily payment flows, equivalent to between one and eleven times daily GDP. That’s not good! Fortunately the Fed is there to provide a backstop of liquidity injections, and unlike the pandemic or the current commodity price shock, it is a risk that policymakers have flagged. What It Means for InsurersAnother segment of the financial industry that may be impacted is insurance. If cyberattacks do wreak damage across US and European computer systems, insurance carriers may have to pick up the tab. But as we discussed last week in the context of aviation insurance, war often renders insurance policies worthless. After NotPetya, several affected multinational corporations approached their insurance companies to claim for damages. They were rebuffed on the basis the event was considered “warlike”. Both Merck and Mondelez took their respective insurance companies to court and in January this year the Superior Court of New Jersey ruled in Merck’s favour; Mondelez is awaiting a decision from a court in Illinois. As a result, insurance companies have been restyling the terms of their policies. One insurance company that is heavily involved is Beazley. The UK-based specialist insurer is one of the leading cyber insurance underwriters in the US. It was an early mover in the category, launching its cyber product in 2009, and has built up a track record of specialist experience. With cyber insurance premiums accounting for only a fraction of the cost of cybercrime, it was seen as a key area for growth. However, managing risk has proven difficult. That’s because cyber is shape-shifting in a way that other insurance lines are not – new means of cyber attack continuously emerge. Five years ago, most claims were linked to data breaches, which Beazley had a good handle on; then they migrated to ransomware attacks. Based on industry data, the frequency of data breach claims fell by 20% between first quarter 2018 and end 2020, while the frequency of ransomware claims rose by 120%. Beazley’s loss rates crept up. The company responded by cutting exposure and increasing prices. Industrywide, cyber pricing increased by 96% in the third quarter 2021, the largest increase since 2015. Beazley brought down its number of policies even while total premiums rose. For banks and for insurance companies, the next few months could present a real test of their risk management capabilities. “This is how they tell me the world ends,” writes Nicole Perlroth. Let’s hope we are prepared. Bloomberg subscribers may have seen that I’ve been writing a bi-weekly column for them since the beginning of the year. So far, I’ve written about bank bonuses, index providers and more. Some of the themes will be familiar to regular Net Interest readers. This week I wrote about central clearing houses and how they exacerbate liquidity strains and promote mispricing of risk in markets. You can read it here. You’re on the free list for Net Interest. For the full experience, become a paying subscriber. |
Older messages
Who Owns All the Planes?
Friday, March 18, 2022
Plus: Trafigura, Credit Cards, London Metal Exchange
Commodities Trading
Friday, March 11, 2022
Plus: London Metal Exchange, Interconnectivity, Interest Rates
Financial Warfare
Friday, March 4, 2022
Plus: Klarna, Goldman Sachs, Car Financing
Swift Sanctions
Friday, February 25, 2022
The Financial System and Foreign Policy
PayPal, 20 Years On
Friday, February 18, 2022
Plus: MoneyGram, Mortgage Rates, Storm Eunice
You Might Also Like
Longreads + Open Thread
Saturday, March 8, 2025
Personal Essays, Lies, Popes, GPT-4.5, Banks, Buy-and-Hold, Advanced Portfolio Management, Trade, Karp Longreads + Open Thread By Byrne Hobart • 8 Mar 2025 View in browser View in browser Longreads
💸 A $24 billion grocery haul
Friday, March 7, 2025
Walgreens landed in a shopping basket, crypto investors felt pranked by the president, and a burger made of skin | Finimize Hi Reader, here's what you need to know for March 8th in 3:11 minutes.
The financial toll of a divorce can be devastating
Friday, March 7, 2025
Here are some options to get back on track ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏
Too Big To Fail?
Friday, March 7, 2025
Revisiting Millennium and Multi-Manager Hedge Funds ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏
The tell-tale signs the crash of a lifetime is near
Friday, March 7, 2025
Message from Harry Dent ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏
👀 DeepSeek 2.0
Thursday, March 6, 2025
Alibaba's AI competitor, Europe's rate cut, and loads of instant noodles | Finimize TOGETHER WITH Hi Reader, here's what you need to know for March 7th in 3:07 minutes. Investors rewarded
Crypto Politics: Strategy or Play? - Issue #515
Thursday, March 6, 2025
FTW Crypto: Trump's crypto plan fuels market surges—is it real policy or just strategy? Decentralization may be the only way forward. ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏
What can 40 years of data on vacancy advertising costs tell us about labour market equilibrium?
Thursday, March 6, 2025
Michal Stelmach, James Kensett and Philip Schnattinger Economists frequently use the vacancies to unemployment (V/U) ratio to measure labour market tightness. Analysis of the labour market during the
🇺🇸 Make America rich again
Wednesday, March 5, 2025
The US president stood by tariffs, China revealed ambitious plans, and the startup fighting fast fashion's ugly side | Finimize TOGETHER WITH Hi Reader, here's what you need to know for March
Are you prepared for Social Security’s uncertain future?
Wednesday, March 5, 2025
Investing in gold with AHG could help stabilize your retirement ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏